IT Domain Knowledge
Network Monitoring is a never-ending process that needs constant attention. In the IT jungle, one could easily get lost in the sea of devices and configuration settings. Our solution, is IT driven network management system, offers the best-in-class network monitoring with real-time monitoring and intelligent alerts that predict failures before they happen! The only way to know if everything on a network is operating efficiently is with a network monitoring tool like GEMS.
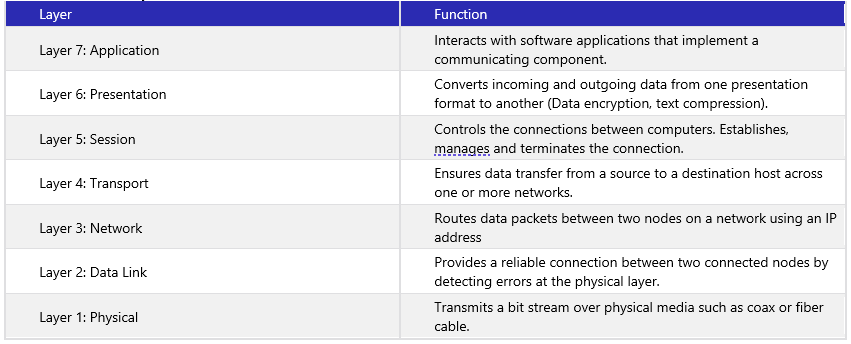
Understanding of basic networking begins with the Open Systems Interconnect model.
The OSI model standardizes the key functions of a network using networking protocols. This allows different domains and devices types from different vendors to communicate with each other over a network. In the OSI model, network communications are grouped into seven logical layers.
The OSI Seven Layer Model
Why is it important to monitor networks? Every company in the world has IT assets that enable faster, more efficient and more profitable business operations. IT assets create competitive advantages for companies but only if these systems is available. With many IT assets, there is no backup plan in the event of a loss. This is why the network is so important. It connects everything together and makes it possible for the IT infrastructure to function.
Networks are dynamic environments. GEMS is a solution for Network Admins to support new users, technologies and applications without impacting network performance. We've taken the guesswork out of managing your network with need-to-know information at your fingertips. It's the only network management solution that provides visibility to all areas of your network in one place.
When network problems arise, with GEMS is the new generation of root cause analysis. What is GEMS? GEMS is a proactive network monitoring tool that can quickly identify the root cause of network performance problems before they impact users, applications, and the business. You can use GEMS to pinpoint where in the network an issue is - so you can spend more time solving it and less time finding it.
SNMP software agents communicate with network management systems to relay information on device and service status and configuration. The NMS provides a single interface for all your commands and alerts. You can batch multiple commands at once and get automatic notifications whenever something needs attention. SNMP overcomes shortcomings of other protocols thanks to the concept of a MIB.
The MIB is a technical description for describing the components and status information of a network device. MIBs can be created for any device in the IoT. They cover things like IP video cameras, vehicles, and industrial equipment. There's also an SNMP system that lets you monitor services such as Dynamic Host Configuration Protocol (DHCP) and ensure devices are running properly.
SNMP is a push and pull between network devices and the Network Management System (NMS). SNMP agents, who live with the MIB on a network device, collect information constantly but only push it over to the NMS when they are requested or when some aspect of the network crosses a pre-defined threshold known as a trap. Firing a trap is a great way to keep track of the issues that pop up. It allows you to remember those moments which could be important, errors or not.
SNMP also includes an inform message type that enables a network monitoring tool to acknowledge messages from a device. Trap is an SNMP operation that enables devices to send messages to SNMP management applications. The following is an example of a simple SNMP trap message:"management station HOST-1 sends trap message with text 'Hello world!' and hexadecimal value 0x0201." Inform messages allow agents to reset triggered alerts. Network management tools also can change a network device through the SNMP agent by sending a set message.
The NMS can also use a set message to make changes to a network device through the SNMP agent. This capability allows the network manager to make changes to the device configuration in response to new-network events. Often, SNMP functions in a synchronous model, in which the SNMP manager initiates the communication, and the agent responds to it. Typically, SNMP uses User Datagram Protocol (UDP) as its transport protocol. Well-known UDP ports for SNMP traffic are 161 (SNMP) and 162 (SNMPTRAP). They are the same in all versions of SNMP and should not change. SNMP commands can be used to perform tasks like resetting passwords, changing configuration settings, and reporting how much bandwidth, CPU and memory are in use.
SNMP is supported on a wide range of hardware. For example, you can find it in your router, switch, and wireless access point as well as in endpoints like your printer, scanner or IoT devices.
Components of SNMP
There are four main components to an SNMP-managed network. It includes the following:
- SNMP agent
Agent software is installed on the device or service that you want to monitor it. The software collects data about disk space, bandwidth use and other important network performance metrics. These agents use SNMP protocols to communicate with the manager. When queried by it, the agent sends the requested information back to the management system. If an error occurs, agents will proactively report it to the NMS. Most devices come with an SNMP agent pre-installed, but you usually need to set it up and turn it on.
- SNMP-managed network nodes
These are the network devices upon which agents run.
- SNMP manager
The NMS is a software platform that functions as a centralized console to which agents feed information about their environment and which the NMS gathers, aggregates, and displays data. The NMS may also be configured to send commands to agents. The NMS will actively request agents to send updates at regular periodically. The features available in the NMS will determine how widescale they can manage and monitor a network.
- Management information base
The MIB Database is a text file that lists all objects on a device that can be queried or controlled using SNMP. Every MIB item is given a unique OID.
SNMP commands
SNMP can perform a multitude of functions, usines a push and pull between network devices and the Network Management System (NMS). It can issue commands to read and write, such as resetting a password or changing a configuration setting. SNMP managers can monitor several indicators of performance such as CPU and memory metrics and automatically email or text alerts when specific thresholds are reached. Most of the time, SNMP operates in a synchronous model--it is initiated by the SNMP Manager and there is a response. These commands and messages, typically transported over TCP/IP or UDP, are known as protocol data units (PDUs).
These are some commonly used SNMP commands as follow.
- GET Request: Sent by the SNMP manager and received by an agent, to obtain the value of a variable identified by its OID, in an MIB.
- GETBULK Request: Sent by the SNMP manager to the agent to efficiently obtain a potentially large amount of data, especially large tables.
- GETNEXT Request: Sent by the SNMP manager to the agent to retrieve the values of the next OID in the MIB's hierarchy.
- INFORM Request: An asynchronous alert like a TRAP but requires confirmation of receipt by the SNMP manager.
- RESPONSE: Sent by the agent to the SNMP manager, issued in reply to a GET Request, GETNEXT Request, GETBULK Request and a SET Request. Contains the values of the requested variables.
- SET Request: Sent by the SNMP manager to the agent to issue configurations or commands.
- TRAP: An asynchronous alert sent by the agent to the SNMP manager to indicate that something significant event has happened, such as an error or failure, has occurred.
The SLA is a contract between IT and Line of Business Owners that commits to providing a certain level of network performance and uptime. It is often created after a business-wide assessment, so it can be tailored to the needs of each individual organization. SLAs are a commitment by a service provider to their customer that the provider will deliver a predefined level of service. SLAs are often used to provide a level of performance guarantee. They are normally measured and reported on for performance management purposes, and might be tied to IT compensation plans.
Why are SLAs important? Because poor performance and down time is costly. For an e-Commerce website like Amazon, one hour of downtime can cost millions in lost revenue.
Companies across the world use a network monitoring system to ensure security, prevent downtime and protect against cyber-attacks. Network monitoring systems poll network devices and servers for performance data using standard protocols such as SNMP, WMI, NetFlow and more. These systems are an integral part of any business's IT infrastructure using standard protocols such as:
- SNMP, Simple Network Management Protocol
- WMI, Windows Management Instrumentation
- SSH, Secure Shell for Unix and Linux server
- The two most widely used monitoring protocols are SNMP and WMI.
- Simple Network Management Protocol (SNMP)
SNMP is an Internet Standard protocol for collecting and organizing information about managed devices on IP networks and for modifying that information to change device behaviour. Devices that typically support SNMP include cable modems, routers, switches, servers, workstations, printers, and moreSNMP is standard protocol that collects data from almost any network attached device, including: Routers, Switches, Wireless LAN Controllers, wireless Access Points, Servers, Printers and more.
SNMP works by querying “Objects”. An object is something that an NMS collects information about. For instance, CPU utilization is an SNMP object. Querying on the CPU utilization object would return a value that an NMS uses for alerting and reporting.
The Objects queried by SNMP are maintained in a Management Information Base, or MIB. The Management Information Base (MIB) can be thought of as a database of managed objects that the agent tracks. Any sort of status or statistical information that can be accessed by the NMS is defined in a MIB. For example, the MIB for a Cisco router will contain all objects, defined by Cisco, that can be used to monitor that router such as CPU utilization, memory utilization and interface status.The objects in a MIB are catalogued using an standardized numerating system. Each object has its own, unique Object Identifier, or OID.
Some NMSs provides a MIB Browser. A MIB Browser allows Network Admins navigate thru a MIB to find additional objects that they want to monitor on a device.
Windows Management Instrumentation (WMI)
WMI (Windows Management Instrumentation); It is a technology that enables almost every object to be controlled in Windows operating systems and can perform operations and management functions in the operating system. This protocol creates an operating system interface that receives information from devices running a WMI agent. The WMI gathers details about the operating system, hardware or software data, the status and properties of systems, configuration and security information, and process and services information. Then sent all of these detail data along to the network management software, which monitors network health, performance, and availability.
VPN stands for Virtual Private Network. It is a method by which two end-points create a single, private connection, or tunnel, while using a larger network infrastructure such as the internet or wide area network. When established, a VPN acts like a direct connection to a private network. The VPN itself simply acts like a network interface to the client and is transparent the operating system, applications, and users accessing the VPN network. Therefore, applications, messages, and users can all use the connection normally without any need to understand how the VPN operates.
How to create a VPN
A traditional VPN requires two endpoints. One is the remote endpoint and the other is the local endpoint. To create the VPN connection, on both endpoints must match or support the VPN methodology used on the other endpoint. Once both endpoints have been established VPN connection, they create a connection called a VPN tunnel.
Types of VPN
Remote client
In this type of VPN, the remote user must have a VPN client installed and configured to connect to a VPN gateway on the local network.
Site-to-site
Another commonly used form of VPN allows for a WAN-style connection between two different sites by using a public network such as the internet rather than going through the expense and difficulty of installing a direct, private connection.
Client-to-provider
A VPN, which connects you to a VPN provider who in turn has a network connection to the internet, is becoming increasingly common. The user must have a VPN client installed and configured to connect to the remote VPN provider’s VPN servers. The VPN connection only lasts for the first part of the connection and not all the way to the destination.
VPN components
A VPN works by establishing a secure, point-to-point connection between the remote client and a VPN server connected to the target network. A VPN connection establishes a secure channel to route data & IP header on the local network. Once established, it encapsulates and encrypts both behind the remote endpoint.. An IP header designed to route across the insecure, public network is added, and then the data is ready for send it across a public network.
VPN clients
Standalone VPN clients
Standalone VPN clients require the installation of software on one or both endpoints. In-order to establish a VPN connection, the endpoint must run the VPN client and connect to the other endpoint.
Built-in OS VPN Clients
All major operating systems, including Windows, iOS, MacOS, Android and Linux make it easy to connect to third-party VPN servers. It's just a matter of ensuring the remote VPN endpoint supports the same protocol and configurations. These clients are often not easily configured by non-technical users. They are therefore most often used in a corporate environment.
VPN server
A remote endpoint that connects to a VPN server also typically features a client which supports all the VPN server settings. Typically, this means that the VPN sever should act as both a gateway and router (at least) at the edge of one's local network or computer system. The server is responsible for unfolding the packets and reshaping them so they can be distributed to the local network or internet.
Tunneling protocol
A VPN which aims to connect you to a public network must establish a regular non-VPN connection with that network. This is done by way of tunneling protocols. A tunneling protocol (e.g., the Virtual Private Network Protocol) wraps each transmitted packet such that it can be read and transmitted across networks that are not private.
An IP address is a unique identifier for every machine using the Internet. Known as your “internet protocol address,” this identifier is written as a string of numbers separated by periods. The Internet Protocol (IP) is part of the Internet layer of the Internet protocol suite. In the OSI model, IP would be considered part of the network layer. IP is traditionally used in conjunction with a higher-level protocol, most notably TCP. The IP standard is governed by RFC 791.
Most addresses are IPv4. It’s the most widely-deployed IP used to connected devices to the Internet. Addresses in IPv4 are 32-bits long. This allows for a maximum of 4,294,967,296 (232) unique addresses. IPv6 is the most recent version Addresses in IPv6 are 128-bits, which allows for 3.4 x 1038 (2128) unique addresses. IP addresses are binary numbers but are typically expressed in decimal form (IPv4) or hexadecimal form (IPv6) to make reading and using them easier for humans.
An IP address is a unique identifier assigned to a device or domain that connects to the Internet. This means that IP must work without a central directory or monitor, and that it cannot rely upon specific links or nodes existing. IP is a connectionless protocol that is datagram-oriented., so each data packets must contain the source IP address, destination IP address, and other data in the header to be successfully delivered. Combined, these factors make IP an unreliable, best effort delivery protocol. An IP error correction is handled by upper level protocols instead. These protocols include TCP, which is a connection-oriented protocol, and UDP, which is a connectionless protocol. Most Internet traffic is TCP/IP.
IPv4 address
The original IPv4 specification was designed for the ARPANET in 1983 network that would eventually become the internet. Originally a test network, no one contemplated how many addresses might be needed in the future. At the time, the 232 addresses (4.3 billion) were surely considered sufficient. However, over time, it became obvious that as currently implemented, the IPv4 address space would not be big enough for a worldwide internet with numerous connected devices per person.
IPv6 addresses
o avoid the seemingly reoccurring issue in technology, where a specification’s limitation seems more than sufficient at the time, but inevitably becomes too small, the designers of IPv6 created an enormous address space for IPv6. The address size was increased from 32 bits in IPv4 to 128 bits in IPv6.
The IPv6 has a theoretical limit of 3.4 x 1038 addresses. That’s over 340 undecillion (340 trillion trillion trillion) addresses, which is make sure that every single atom on earth has one IP address.
On the Internet, name resolution is handled by the Domain Name System (DNS). DNS is a directory of names that match with numbers. The numbers, in this case are IP addresses, which computers use to communicate with each other. When the connection is initiated, the source host will request the IP address of the destination host from a DNS server. The DNS server will reply with the destination’s IP address. This IP address will then be used for all communications sent to that name.
Ping (Packet Internet or Inter-Network Groper) is a computer network administration utility command to test available on virtually any operating system with network connectivity, that acts as a test to see if a networked device is reachable.
The ping command sends a request over the network to a specific device. A successful ping results in a response from the computer that was pinged back to the originating computer.
Ping and speed test
The term is also used to test and determine how fast a data signal travels from one place, like a computer, to another, like a website.
Ping works by sending an Internet Control Message Protocol (ICMP). The ping a command-line based utility, ping lends itself to easy use in various scripts, allowing for numerous pings to run and be recorded for all type of usage.
Troubleshooting with Ping
Perhaps the most common use of the ping utility is in troubleshooting. When trying to use applications or systems over a network, the most important thing to know is if there is actually a working connection or device. When a ping command is issued, a ping signal is sent to a specified address. When the target host receives the echo request, it responds by sending an echo reply packet. A quick ping by IP address will confirm that the system is on, that there is a connection, and that the two machines can talk to each other.
Ping IP address
Ping error
If ping gets no response from the target host, most implementations of ping display nothing or a timeout notification. The result may look like this, for example:
- Pinging 121.242.124.9 with 32 bytes of data:
- Request timed out.
- Request timed out.
- Request timed out.
- Request timed out.
Discovery
Ping can be used as a quick and dirty discovery tool. Since virtually any network connected device will respond to a ping, pinging a range of addresses.
Monitoring
Ping can be used to monitor the network availability of devices. When a ping command ıssued as a scheduled task can offer simple polling of any networked computer or device without the need to install any additional software agents, and without the need to open additional ports. The simplest any up/down monitor could be accomplished by running a ping until stopped. When the pings start failing, there is an issue reaching the link or device
Measuring Latency
round-trip time (RTT) or latency, is a measure of how long it took to receive a response. Measured in milliseconds (ms), the process starts when a when pink request issued to a server and is completed when a response from the server is received packet.
Bandwidth (BW) is measured as the amount of data that can be transmitted from one point to another within a network in a specific period. And bandwidth is expressed as a bitrate and measured in bits per second (bps).
The term bandwidth in general implies capacity. Bandwidth is also a key concept in several other technological fields. In a transmission such as a radio signal and is typically measured in hertz (Hz).
Expressing bandwidth
As mentioned earlier, Bandwidth is measured in bits per second and expressed in bps. However, today's networks typically have capacities that are too large to be expressed in bps, so they cannot be easily expressed using such small units. It's now common to see higher numbers denoted by the metric power of 10, such as Mbps (megabits per second), Gbps (gigabits per second), or Tbps (terabits per second).
- K = kilo = 1,000 bits. =10³
- M = mega = 1,000 kilo = 1,000,000 bits.=10⁶
- G = giga = 1,000 mega = 1,000,000,000 bits. =10⁹
- T = tera = 1,000 giga = 1,000,000,000,000 bits.=10¹²
After terabit, there are petabit, exabit, zettabit, and yottabit, each representing an additional power of 10.
NetFlow is a network protocol developed by Cisco Systems that allows administrators to collect and analyze data on network traffic flows. It is often used for network performance monitoring and troubleshooting, security, and capacity planning.
NetFlow works by capturing information about each individual flow of traffic passing through a network device, such as a router or switch. This information includes the source and destination IP addresses, port numbers, and protocol. The collected data is stored in a flow record and can be analyzed to gain insights into network traffic patterns and trends.
There are several versions of the NetFlow protocol, including NetFlow v1, v5, v7, v8, and v9. Each version has its own set of features and capabilities and is designed to meet the specific needs of different environments and use cases.
NetFlow data is typically collected by a NetFlow collector, which is a separate server or computer running a NetFlow receiver. NetFlow data is typically exported using UDP and sent to the collector's IP address and a configured destination port. In some cases, SNMP can be used to turn on NetFlow and configure the collector's IP address.
NetFlow data can also be accessed through the NetFlow MIB, which allows for the gathering of data via SNMP. This data includes upstream/downstream traffic and packets/bytes per flow, as well as information on "top talkers" and other traffic types.
A network diagram provides a visual representation of a network, displaying how the individual elements work interact. . Depending on the scope and purpose, a network diagram may provide a simple overview of the network or a more detailed network diagram. There are two main types of network diagrams: physical and logical. Physical network diagrams.
Physical Network Diagrams
A physical network diagram, as its name suggests, shows the actual physical arrangement of the network elements and cable connections. Physical network diagrams shows all of the physical aspects of the network, likely include: ports, cables, racks, servers, specific models, and so on. Within the OSI model of networking, physical diagrams are referred to as ‘L1’
Logical Network Diagrams
A logical network diagram (Layer 3) addresses how information in the network flows. This means that you’ll generally visualize the following elements in your logical network topology:
- subnets (such as: IP addresses, VLAN IDs, and subnet masks,)
- network objects (routers and firewalls)
- network segments
- specific routing protocols
- routing domains
- traffic flow
- voice gateways
Protocols are the foundation of modern communication systems, ensuring smooth and uninterrupted connectivity between different networks. When it comes to seamless transitioning between terrestrial networks, such as 6G, and satellite networks for satellite roaming such as 7G, protocols play a crucial role in facilitating a seamless handover of connections. Let's delve deeper into the various protocols and their specific roles in achieving this objective.
- Handover/Handoff Protocols: Handover protocols are essential for managing the transfer of an ongoing communication session from one network (terrestrial) to another (satellite) without any interruption. These protocols ensure that the connection is seamlessly handed over to the satellite network while maintaining the continuity of the session. Handover protocols handle tasks such as signaling, authentication, and negotiation between the networks involved. They facilitate a smooth transition, allowing the user to seamlessly switch between networks without experiencing any disruption in the service.
- Authentication and Authorization Protocols: During the handover process, authentication and authorization protocols play a critical role in verifying the identity of the user or device. These protocols ensure that the user or device is authorized to connect to the satellite network and access its services. By establishing secure communication channels and validating credentials, authentication and authorization protocols maintain the integrity and security of the roaming connection. They protect against unauthorized access and ensure that only legitimate users can seamlessly transition between networks.
- Network Discovery and Selection Protocols: To achieve seamless transitioning, it is crucial to identify and select the most suitable network, whether terrestrial or satellite, based on factors such as signal strength, quality, coverage, and user preferences. Network discovery and selection protocols assist in this process by scanning the available networks in the vicinity and autonomously determining the best network to connect to. These protocols enable devices to make informed decisions and select the appropriate network for a seamless transition. By considering various network parameters, they optimize the handover process and enhance the overall user experience.
- Signal Control and Adaptation Protocols: Seamless connectivity during satellite roaming requires efficient signal control and adaptation to account for the differences between terrestrial and satellite networks. Signal control and adaptation protocols manage the various aspects of signal characteristics, including modulation schemes, coding techniques, frequency bands, and signal strength. These protocols ensure that the communication parameters are adapted and optimized during the handover process to maintain data transmission continuity and maximize performance. By dynamically adjusting the signal parameters, they enable a seamless transition and ensure uninterrupted connectivity for users.
- Quality of Service (QoS) Protocols: Maintaining a consistent level of service is crucial during satellite roaming. QoS protocols prioritize and manage data traffic to ensure a satisfactory user experience. These protocols allocate network resources based on the prioritization of critical data streams. By optimizing bandwidth utilization, reducing latency, and managing network congestion, QoS protocols enhance the quality and reliability of the communication during the handover process. They ensure that the user's service requirements are met, regardless of whether they are connected to a terrestrial or satellite network.
- Network Protocols: Standard network protocols, such as Internet Protocol (IP), Transmission Control Protocol (TCP), and User Datagram Protocol (UDP), are vital for carrying data packets over both terrestrial and satellite networks. These protocols facilitate end-to-end communication, routing, error detection, and data integrity across the interconnected networks. By adhering to standardized protocols, devices can seamlessly exchange data packets between different networks, ensuring consistent connectivity and reliable communication during the handover process.
- Internet Protocol (IP): Think of IP as the language that devices on a network use to communicate with each other. It provides a unique address, called an IP address, to each device connected to the network. IP is responsible for routing data packets (chunks of information) from the source device to the destination device over the internet or any network. It ensures that the data reaches the right place by using the IP addresses and making sure the packets are delivered correctly.
- Transmission Control Protocol (TCP): TCP is like a reliable delivery service for data packets. It ensures that data is sent accurately and in the correct order between devices. TCP breaks down the data into smaller packets, adds sequence numbers to them, and ensures they are reassembled correctly at the receiving end. It also handles error detection and retransmission if any packets are lost or damaged during transmission. TCP guarantees that the data arrives complete and in the right order, which is crucial for tasks like downloading files, sending emails, or browsing the web.
- User Datagram Protocol (UDP): UDP is similar to TCP but less reliable. It's like a fast courier service that delivers packets without worrying too much about accuracy or order. UDP is commonly used for real-time applications where speed is more important than reliability, such as video streaming or online gaming. It sends packets quickly without waiting for acknowledgments or retransmissions, which can lead to some packets being lost or arriving out of order. However, this speed comes at the cost of potential data loss or errors.
These three protocols work together to ensure smooth communication across networks. IP handles the addressing and routing of data packets, while TCP ensures reliable and ordered delivery of the data. UDP, on the other hand, prioritizes speed over reliability and is used for time-sensitive applications. By using these standardized protocols, devices can connect and communicate effectively, ensuring that data is sent and received correctly between different networks.
Network devices, often referred to as networking hardware, are essential for ensuring smooth communication and interconnectivity within a network. Each piece of this hardware has a designated function or responsibility within the network and its various segments. For instance:
- Traffic Management: Devices like routers and firewalls are pivotal for network administrators to oversee and regulate the flow of data across different segments or subnets of a network. They also play a crucial role in preventing unauthorized access.
- Network Linking: Devices such as routers have the capability to bridge distinct networks by utilizing specific protocols. In a similar vein, gateways facilitate communication between systems that operate on different protocols by translating data formats.
- Network Partitioning: One of the primary roles of network devices is to segment a network into separate zones or subnets. This segmentation is vital as it restricts the reach of potential cyber attackers within the network.
These devices function by amplifying, merging, or relaying data packets in accordance with certain network protocols. The configuration of these devices also determines the structure or topology of the network, with common topologies being mesh, bus, ring, star, and tree. While wireless network devices utilize radio frequency signals for data transfer, their wired counterparts depend on cables for communication between different nodes. Regardless of being wired or wireless, networks employ several communication protocols, like TCP and HTTP. All devices within the network are bound by the guidelines set by these protocols when transmitting or receiving data. These protocols also define the behavior of devices within the network.
- Hub: This device broadcasts incoming data packets to all its connected devices without discerning the intended recipient. Due to the lack of packet filtering, hubs can become performance chokepoints in high-traffic networks. While passive hubs merely relay data packets, active hubs amplify or rejuvenate the signal before dispatching it, functioning similarly to repeaters. Both types can be configured to handle both analog and digital signals.
- Switch: A switch, equipped with multiple ports, is engineered to direct incoming data packets to the appropriate ports or devices based on the MAC address. Being more sophisticated than a hub, it enhances network efficiency with features like smart packet forwarding and supports full-duplex communication. Some advanced switches, known as multi-layer switches, can also function as routers.
- Router: This widely-used networking device can merge two or more network segments or subnets, forming a larger network. Operating at the network layer, routers maintain a routing table containing information like IP addresses of connected devices, aiding in directing packets to their intended destinations.
- Bridge: Functioning at the data link layer, a bridge connects two LANs that use identical protocols. Although they can smartly forward packets like switches, they typically have only one input and output port.
- Gateway: This advanced device provides data format conversion and protocol adaptation. For instance, routers can serve as gateways by adjusting incoming data to meet the requirements of the destination network's protocol.
- Modem: Primarily, modems convert analog signals to digital and vice versa. They are commonly found at the endpoints of traditional phone lines that provide DSL services.
- Repeater: Operating at the OSI Layer 1, repeaters amplify signals, enabling data transmission over extended distances.
- Access Point (AP): An AP, a device that bridges wireless and wired LANs, comprises a transmitter, receiver, and an inbuilt antenna. Its transmission range is influenced by environmental factors and obstacles. Some advanced APs can also function as switches, firewalls, or DHCP servers.
Ensuring the consistent monitoring of network devices is pivotal for the stability and effectiveness of a network system. Being proactive in this monitoring can mitigate unexpected disruptions or lags in network resources. The key motivations for such monitoring encompass:
- Prompt Problem-Solving: Ongoing monitoring empowers IT professionals to swiftly detect and rectify issues related to the performance and uptime of network devices.
- Reduced Network Interruptions: Immediate notifications about potential complications enable network managers to act swiftly, minimizing the risk of prolonged network disruptions.
- Enhanced Network Safeguarding: Consistent oversight aids in recording security incidents, spotting atypical data flow, and checking for potential security gaps, fortifying the network's defense mechanisms.
- Augmented Network Transparency: Systematized monitoring grants instantaneous updates on the adherence status, configuration details, and the general well-being of network devices, enriching the clarity and management of the network framework.
To encapsulate, while network devices form the backbone facilitating data interactions within a network, the surveillance of these devices is indispensable for their peak functionality, safeguarding, and dependability.
