GEMS: The Complete Network & Application Monitoring Solution
Discover the power of GEMS, the comprehensive and affordable full stack network and application monitoring tool that provides real-time visibility and proactive troubleshooting capabilities for all your systems. With GEMS, you can ensure the smooth operation of your networks, identify issues before they impact your customers and business, and optimize your network performance.
Real-Time Visibility and Troubleshooting:
With GEMS, gain real-time visibility into the health and performance of your network infrastructure. Our versatile and affordable solution empowers you to proactively troubleshoot any issues that may arise, ensuring seamless network operations and delivering exceptional customer experiences.
Key Features:
GEMS: The Complete Network & Application Monitoring Solution
Real-Time Visibility and Troubleshooting: With GEMS, gain real-time visibility into the health and performance of your network infrastructure. Our versatile and affordable solution empowers you to proactively troubleshoot any issues that may arise, ensuring seamless network operations and delivering exceptional customer experiences.
Key Features:
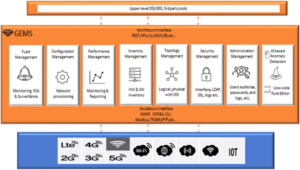
- Comprehensive FCAPS Compliance: Ensure robust network management with GEMS' comprehensive FCAPS compliance. Take complete control and oversight of your network infrastructure, covering fault management, configuration management, performance management, and more.
- Centralized Configuration: Streamline your network configuration process with GEMS' centralized configuration management. Effortlessly configure, reconfigure, and monitor the performance of all your devices, ensuring they function exactly as expected.
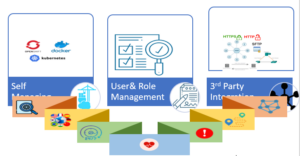
- Seamless Integration with Other Network EMSs: Experience easy integration with other network Element Management Systems (EMSs) through GEMS' seamless integration capabilities. Maximize the value of your existing infrastructure by incorporating GEMS into your network management ecosystem.
- Low CAPEX & OPEX: GEMS offers a cost-effective solution with low capital and operational
 expenditures. Enjoy the benefits of a versatile and comprehensive network monitoring tool without breaking your budget.
expenditures. Enjoy the benefits of a versatile and comprehensive network monitoring tool without breaking your budget.
- Multi-Vendor and Multi-Domain Platform: GEMS supports multi-vendor and multi-domain networks, providing a complete view of your network infrastructure regardless of vendor, technology, or domain. Consolidate your network management efforts into a single, adaptable platform.
- AI-Based Anomaly Detection: Enhance your network security and performance with GEMS' AI-based Anomaly Detection Module. Utilize intelligent algorithms to track performance metrics, identify anomalies, and mitigate potential threats in real-time.
- Customizable Dashboards and Reporting: Tailor your monitoring experience with GEMS' customizable dashboards and reporting capabilities. Visualize key performance indicators (KPIs) and KPI threshold management, create personalized reports, and monitor network capacity and bandwidth utilization.
- Inventory Management: Stay on top of your network hardware equipment and software versions with GEMS' inventory management functionality. Easily search, examine, and consolidate resource data from across your managed network.
- Topology Management: Gain hierarchical and scalable views of your entire network with GEMS' topology management. Monitor the physical and logical (L2/L3) layout of your network elements, and capture correlations between network systems in real-time.
 Low-Code Rule Editor and Automation: Simplify the modelling and analysis of your IT and Telco systems with GEMS' low-code rule editor and automation capabilities. Implement affordable and intelligent solutions that trigger actions or call external services, ensuring efficient system behaviour analysis.
Low-Code Rule Editor and Automation: Simplify the modelling and analysis of your IT and Telco systems with GEMS' low-code rule editor and automation capabilities. Implement affordable and intelligent solutions that trigger actions or call external services, ensuring efficient system behaviour analysis.
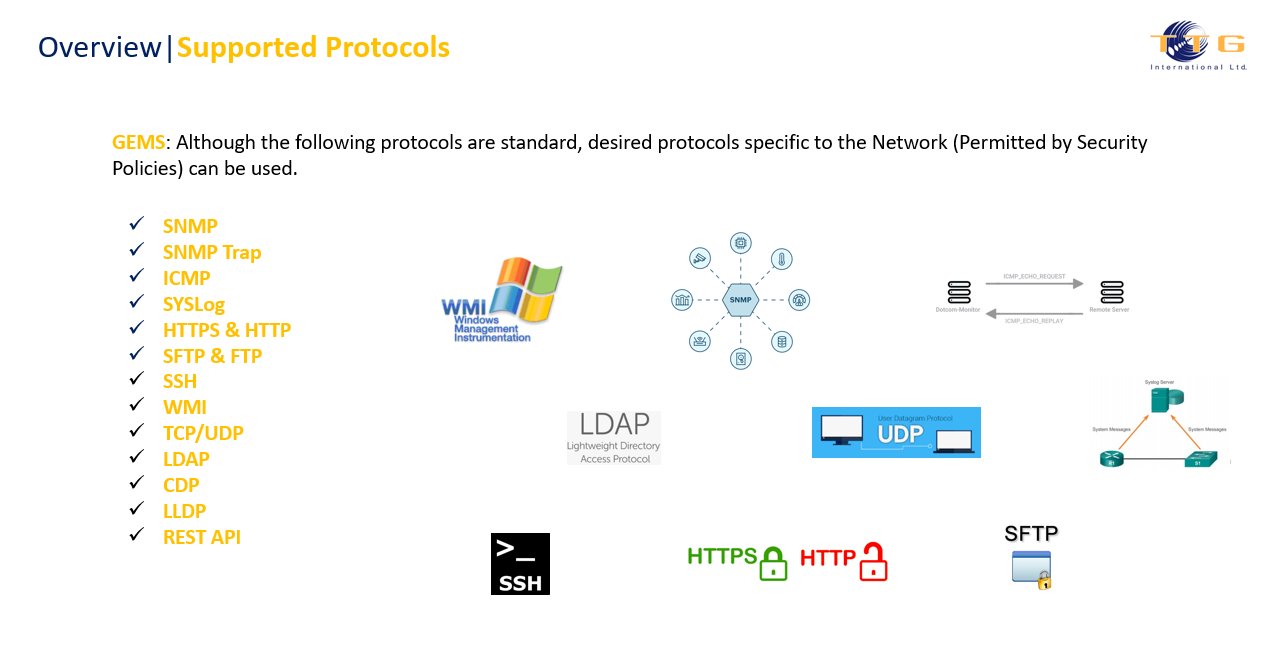
Supported Protocols
Click to Learn more on GEMS use case




 expenditures. Enjoy the benefits of a versatile and comprehensive network monitoring tool without breaking your budget.
expenditures. Enjoy the benefits of a versatile and comprehensive network monitoring tool without breaking your budget. Low-Code Rule Editor and Automation: Simplify the modelling and analysis of your IT and Telco systems with GEMS' low-code rule editor and automation capabilities. Implement affordable and intelligent solutions that trigger actions or call external services, ensuring efficient system behaviour analysis.
Low-Code Rule Editor and Automation: Simplify the modelling and analysis of your IT and Telco systems with GEMS' low-code rule editor and automation capabilities. Implement affordable and intelligent solutions that trigger actions or call external services, ensuring efficient system behaviour analysis.